Understanding Intelligence
Intelligence is the processed and classified information that is elucidated by expert analysts. It is extracted from all sorts of reliable resources and is evaluated for pertinence. It is essential to understand that data or information alone cannot be mislabeled as “intelligence.” Intelligence helps not only the organization in providing relevant information about the loopholes in the organization’s IT infrastructure but also analysts to build a defensive mechanism for the target organization. This section discusses intelligence terminology; the difference between intelligence, information, and data; and concepts related to the background of intelligence-led security testing.
What Is a Threat?
A cyber threat is a possibility of performing malicious actions to damage the critical IT resources of a target organization. Organizations must understand themselves before they can understand what constitutes a threat to them This is one of the most significant pitfalls in the Threat intelligence Community. Without a good knowledge of the business operations and goals, network and its assets, and information such as software versions and hardware choices, it is difficult to identify what constitutes a threat.
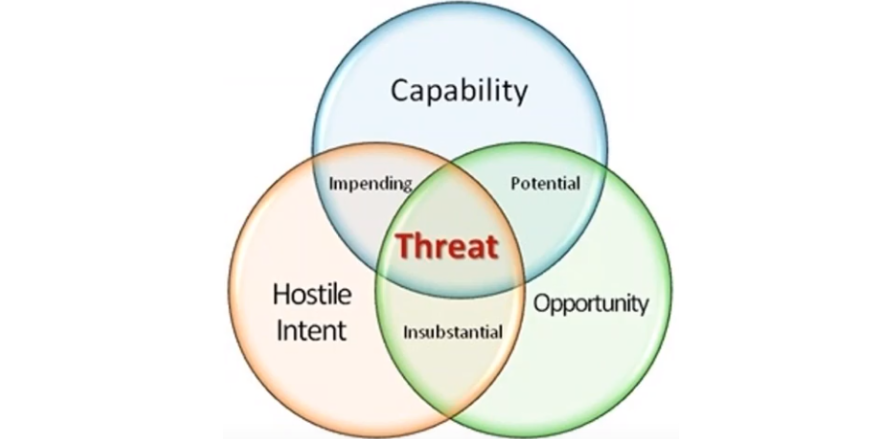
- Organizations must know what their threats are to accurately collect and use threat intelligence
- Threats can be established by evaluating
- Capability + Intent + Opportunity
Just because something is a piece of malware or a vulnerability does not mean it is something that can impact an organization. If the vulnerability is for Windows XP but the organization you are at only has Windows 7 and Windows 8 systems, then that vulnerability is not of concern. The UK signals intelligence agency (GCHQ) has the capability and opportunity to pose a significant threat to U.S. intelligence operations. However, there is no hostile intent, so they are not a threat. Getting an organization to the security maturity that it can truly understand what constitutes threats to it should be a major goal of any threat intelligence program. Having that maturity and all the components that go along with it is significant “ahead of the curve” in terms of average organizational security.
What Is an Intelligence?
Before we begin diving into the depths of Cyber Threat Intelligence, it behooves us to engage in a discussion about what intelligence is, in a traditional sense. Primitives in the traditional intelligence domain form the basis around which CT1 has evolved and apply to our domain as it is a subset of traditional intelligence analysis.
So, what is intelligence? This is a broad question with many answers, but in the context of intelligence analysis, we seek a definition that captures the essence of the information we desire in furtherance of our nation-state objectives (be they military, economic, or geopolitical). A fantastic now-declassified discussion is provided by CIA analyst Martin T. Bimfort who pulls together a variety of definitions to formulate one that describes intelligence in the context of classic intelligence analysis:
“Intelligence is the collecting and processing of that in formation about foreign countries and their agents that are needed by a government for its foreign policy and for national security, the conduct of non-attributable activities abroad to facilitate the implementation of feigning policy, and the protection of both process and product, as well as persons and organizations concerned with these, against unauthorized disclosure”
Intelligence is a process that utilizes information to analyze and respond to emerging requirements of an organization. It is an ability to obtain, adapt, alter, extend, and use the information to solve various organizational problems. Intelligence provides solutions to resolve issues arising during unpredictable circumstances in an organization. It is the output obtained from the analysis of information. In this process, intelligence converts the “what” and “how” of the information into the “why” and “when” of the problem-solving process.
Intelligence versus Information versus Data
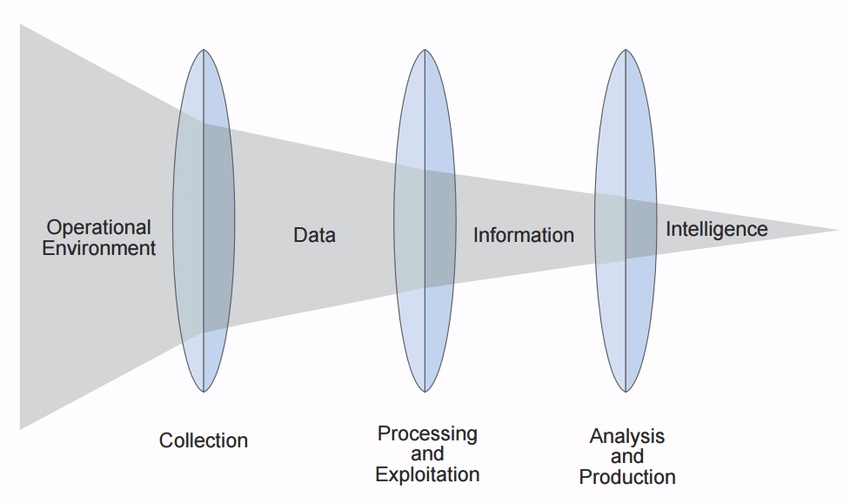
Data in its raw form generally exists in huge volume, defines an object or individual, does not include any context, and is unprocessed. Data itself is not sufficient to solve any problem. It is processed to information and further analyzed to get intelligence from it. This intelligence helps in making decisions to solve various organizational problems. Data can be categorized as either structured data or unstructured data. Structured data consists of numbers, text, etc., whereas unstructured data consists of images, video, audio, etc.
Information is the output of processed data that contains meaning and context. Information is the knowledge, which is produced when a bunch of raw data providing diverse facts about something is combined or interconnected with each other to bring out the broader knowledge about the subject or provide an answer to a query raised by users. It is general knowledge about the things all around in the individual’s environment. It is not restricted and is openly available for everyone to accept and consume.
Intelligence is obtained by processing data and analyzing information. It is interpreted information providing broader in-depth knowledge of the subject (organization, individual, or object) that supports decision-making and response actions. It helps organizations resolve complex problems and is also responsible for interpreting the information and converting it into useful actions or conclusions. In the process of extracting intelligence from information and data, the quantity of the output is reduced, and the value of the output is increased.
Examples in cyber threat intelligence:
This is an IP address (Data)
This IP address is command and control for this malware (information)
The malware is on our systems (information)
We assess that the adversary is not purposely targeting our systems and that this is an incidental infection (Intelligence)
Understanding Cyber Threat Intelligence
Analyzed information about the hostile intent, capability, and opportunity of an adversary.
Cyber Threat Intelligence (CT) is defined as the collection and analysis of information about threats and adversaries and drawing patterns that provide an ability to make knowledgeable decisions for the preparedness, prevention, and response actions against various cyber-attacks.
Cyber threat intelligence helps the organization to identify and mitigate various business risks by converting unknown threats into known threats and helps in implementing various advanced and proactive defense strategies.

